Working with JSON files
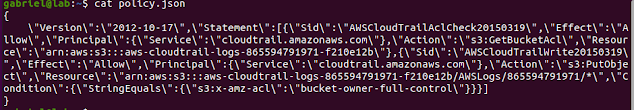
JSON (JavaScript Object Notation) formatted data is pretty much everywhere. As a a lightweight data-interchange format, it has become very popular. I can see it used for all kinds of configuration files (such as AWS policies, for instance), API response data and log data. json.org states that "It is easy for humans to read and write" . Well, anyone who at least once has to debug a long, nested JSON could disagree! JSON is human-friendly only if it is nicely formatted. Fortunately, there are some tools that can help. One of my favorite is underscore-cli, a Node.js tool that can be used as a simple pretty printer. In this example I am going to provide steps for installation on Ubuntu. Installing Node Version Manager and Node.js Install curl: sudo apt-get install curl Install latest nvm: curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.38.0/install.sh | bash Install LTS version of Node.js: nvm install --lts Installing and using underscore-cli npm install ...


